Brave is a new browser from some experienced people that aims to be faster and safer than other browsers by blocking ads and trackers. Brave also wants to disrupt the current online model where users pay for services with their privacy. The About page on Brave's website describes all this, so I won't rehash it. I find the whole concept interesting and I'm curious to see how it turns out.
But since I dissect web browsers for fun, I also was interested to see how Brave looked on disk and what artifacts I could pull from it. I downloaded Brave 0.8 for Windows, installed it, and starting browsing around. After a little bit I closed the browser and found the profile folder, eager to see what new and strange browser artifacts awaited me. Instead, I found the contents very... familiar.
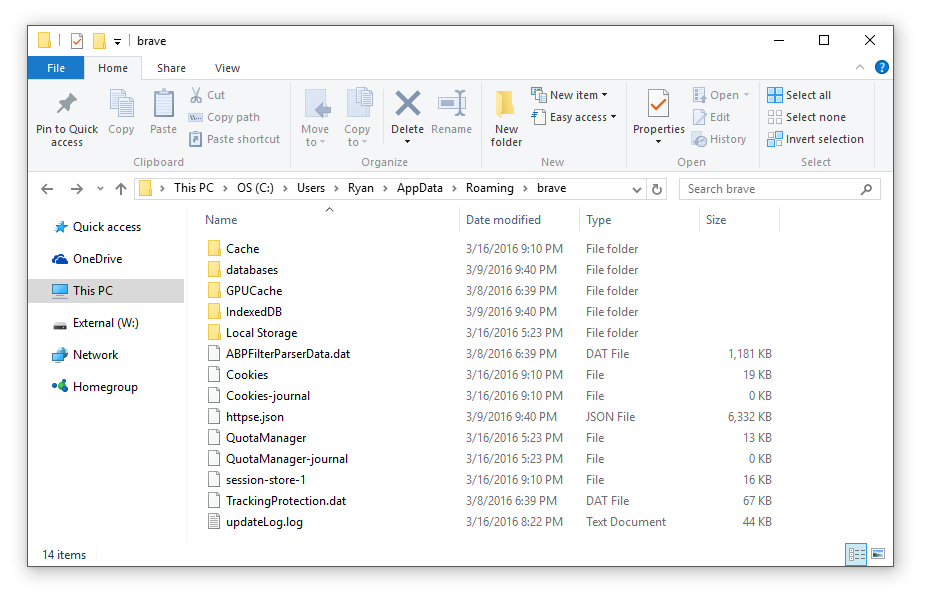
This looks a lot like Chrome! The Brave profile data is located at C:\Users\[User]\AppData\Roaming\brave. The Cookies and QuotaManager SQLite databases are there, as are the Cache/GPUCache directories. Likewise, the Local Storage, IndexedDB, and databases folders are all present and filled with the same stuff as you'd see in Chrome. It turns out that Brave is based in part on Chromium (version 47 as of Brave 0.8). However, there are a good number of files missing that one would expect to see in a Chrome installation; most notably the History SQLite database. The Brave developers have a nice timeline showing what features are planned for what versions of Brave, so it wouldn't surprise me if some other familiar files popped up once things like extensions, autofill, syncing, downloads, and history management are added to the browser.
At least in the short term, it turns out that "session-store-1", one of the new Brave files that is not present in Chrome, maintains the history and session information. It is a JSON file with some of the essentials for browsing visit records: time, location, and page title. Since so many of the Brave artifacts are already handled by Hindsight, I figured I'd build a parser for the session-store file and add it in as well. I've added it to Hindsight v1.6 and to use it, just point Hindsight (with -i) to the Brave profile folder instead of the Chrome profile folder:
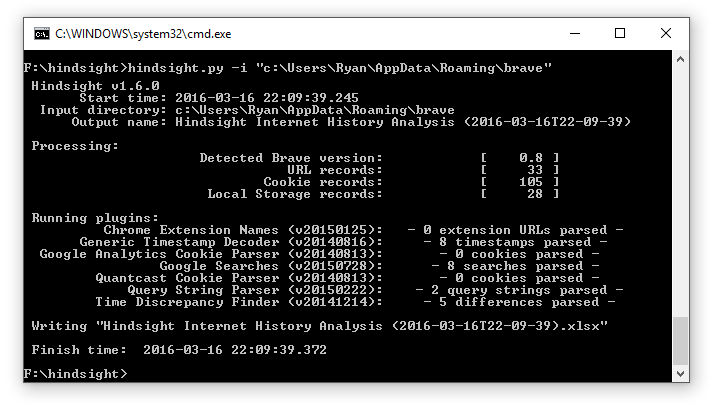
You can get Hindsight from its Github page (https://github.com/obsidianforensics/hindsight). Right now v1.6 (with Brave support) is only available as a Python script (hindsight.py), but I hope to upgrade the exe and GUI versions to v1.6 soon.
Differences
I found a few differences with how Brave does things compared to Chrome, even though many of the data structures are similar. Inside the "brave" folder, sometimes partition folders appear (partition-1, partition-2, etc) that have their own set of Cookies, Cache, and Local Storage. Hindsight will process the contents of these folders as well automatically. With regard to the Cookies database, Brave is not encrypting the cookie values, as Chrome started to do in v33. This makes life a little easier on examiners, but I wouldn't be surprised if this was changed as Brave moves toward (and past) v1.0. I'm also sure that with Brave being rather young and under constant development things will change rapidly under the hood. For that reason, I'm not planning on investing a lot of time in dissecting every current Brave artifact, as things are likely to change. That might change once the browser stabilizes a bit.